Hi,
I’m currently running Xwiki in docker version 14.1-postgres-tomcat.
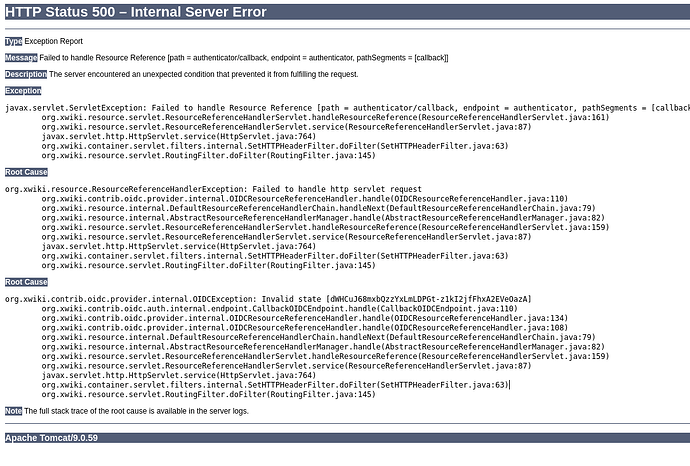
I’ve installed OpenID Connect Authenticator and have run the configuration recommended. When first logging in I’m redirected to Keycloak website. I enter my credentials and then get the following 500 server error.
The rest of the configuration is running nginx proxy in-front forward to docker 8080
I’ve changed settings in xwiki.cfg to include the url, and protocol https.
I’ve updated server.xml to include catalina 8443
<Connector port="8443" protocol="org.apache.coyote.http11.Http11AprProtocol"
maxThreads="150" SSLEnabled="true" >
<UpgradeProtocol className="org.apache.coyote.http2.Http2Protocol" />
<SSLHostConfig>
<Certificate certificateKeyFile="conf/localhost-rsa-key.pem"
certificateFile="conf/localhost-rsa-cert.pem"
certificateChainFile="conf/localhost-rsa-chain.pem"
type="RSA" />
</SSLHostConfig>
</Connector>
<Engine name="Catalina" defaultHost="localhost">
<Valve className="org.apache.catalina.valves.RemoteIpValve"
remoteIpHeader="x-forwarded-for"
requestAttributesEnabled="true"
protocolHeader="x-forwarded-proto"
protocolHeaderHttpsValue="https"/>
Any help here would be greatly appreciated