I’m using keycloak with xwiki using the OpenID Connect extension. Login works pretty good but unfortunately I’m not able to get logout working. If I press logout on xwiki the user will not be logged out but redirected to the current shown xwiki page.
On the keycloak UI I still can see that there is a session for the user.
Further question would be, if a “single log out” should work - means, is the user immediately logged out on xwiki if the user is logged out on a different application which is connected to keycloak, too (and the keycloak session is destroyed for this user).
I guess, the “common” xwiki logout must also send a “logout” to the openid connector like this:
https://keycloak-url/auth/realms/MYREALM/protocol/openid-connect/logout
Is this somehow possible to adapt without changing the code?
Yes this is most probably the problem since right now the authenticator only logout on XWiki side (but indeed if you access a page which is not public then you end up being automatically authenticated again).
Supporting this will definitely need code to be written.
Hi @tmortagne
Thank you very much for your quick answer. I’m a developer and I guess it wouldn’t be to hard to add such functionality. Unfortunately, I don’t have a build / test environment.
I would do it somehow like this:
- add a new logout endpoint to xwiki.properties:
oidc.endpoint.logout=https://keycloak-url/auth/realms/MYREALM/protocol/openid-connect/logout
- In case this is configured, send request to this logout endpoint in the oidc-authenticator/src/main/java/org/xwiki/contrib/oidc/auth/internal/OIDCUserManager.java public void logout() method
what do you think?
Sounds good yes. Just a detail: this code should redirect the user and not send an HTTP request.
Ha maybe not actually, looks like the logout can be done by the relying party too. There is a com.nimbusds.openid.connect.sdk.LogoutRequest helper you can use it seems.
Oh, than its much more difficult if a redirect should be used.
What would happen if the LogoutRequest would be send in the logout() method in OIDCUserManager?
That’s what I tough initially since that’s usually how OIDC works (you make the user do stuff) but read the second part of my previous message.
I have the same Problem and i tried
oidc.endpoint.logout=[site]/auth/realms/aerobase/protocol/openid-connect/logout
in xwiki.properties, but can´t log out.
I´m very interested in a solution for this Problem.
Unfortunately, I’m not able to test it as it looks like, keycloak doesn’t support the RP initiated logout with OIDC. If someone else want to test it, please have a look at the github PR. If necessary, I can provide the compiled *.jar files which needs to be used.
It is just a workaround, but perhaps it’ll help in the meantime:
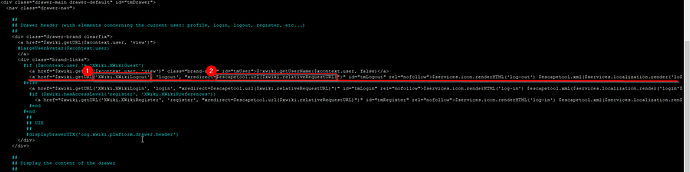
edit the drawer.vm in the /skins/flamingo folder, find the line #1 with XWikiLogout and change #2 (see following picture) to the Keycloak OpenID Logout URL “https://keycloak-url/auth/realms/MYREALM/protocol/openid-connect/logout”.
In my deb-installation the folder is located here: /usr/lib/xwiki/skins/flamingo
Check the syntax, as you must begin directly after the xredirect= an end after URL)
For me this works now for some months. You have to edit it again after an update.
1 Like
It should be possible to fix this problem. Keycloak is not so small, that this is irrelevant.
When RP-initiated logout is not possible, then we need another solution.
We try this “Workaround” but we need a right Solution for this Problem.
With this, no local user (admin) can logout from the Wiki.
Perhaps this can help - but it is just another workaround:
Give the local admins this link:
https://WIKI-ADDRESS/bin/logout/XWiki/XWikiLogout?xredirect=%2Fbin%2Fview%2FMain%2F
If they open this link in the same browser, they should be logged out. But i did not try this!!
I’ve successfully authenticated xwiki with Okta OIDC, but since there is no logout, this renders the OIDC interface unusable/impractical for production use or am I missing something? Did I miss the documentation on the proper URL to call for logout or is the logout function still missing?
It was pretty straight forward to set up with Okta once I figured out the proper login URI. Here is the login redirect URI I used with Okta that got me in:
http://<your_URL_here>:80/oidc/authenticator/callback
<your_URL_here> would be something like wiki.domainname.com
First of all, I found a cool addition to enter a redirect uri to the logout scheme:
http://auth-server/auth/realms/{realm-name}/protocol/openid-connect/logout?redirect_uri=encodedRedirectUri ,
Unfortunately, the whole logout process doesn’t work right now in keycloak. Don’t know why. Maybe related because of using SAML authentication on keycloak for another app, too.
Hi @sbernhard
find the drawer.vm in the /skins/flamingo folder an edit it. search the line with <a href="$xwiki.getURL('XWiki.XWikiLogout', at the beginning. Edit the following and change the whole line:
<a href="$xwiki.getURL('XWiki.XWikiLogout', 'logout', "xredirect=https://KEYCLOAK-SERVER/auth/realms/master/protocol/openid-connect/logout?redirect_uri=ADDRESS_TO_BE_SHOWN_AFTER_LOGOUT"")" id="tmLogout" rel="nofollow">$services.icon.renderHTML('log-out') $escapetool.xml($services.localization.render('logout'))</a>
Afterwards no reboot is needed. Just reload a page. 
Logout will work without problems. I use this for some month now witout problems.
Remember to edit it again, after an update!
Hmm. I use SAML for Nextcloud and Wordpress - and OpenID for Wekan and XWiki. For me it works great.
Works. Thank you very much.
1 Like
Hi all, my workaround is essentially that described by @jwielsch and @sbernhard at post #16, however, I used the Administer Wiki tools to override drawer.vm in my xwiki’s active skin, rather than edit the file directly on the server – hopefully this step means the change will persist across upgrades etc.
Logged in as an administrator > Drawer > Administer Wiki > Look & Feel > Themes > Skin > Customize > Edit this skin > Add a new overriding template names drawer.vm > paste the full contents from server-side file with relevant edit described above > Save
Also, in my case, the location server-side was /usr/local/tomcat/webapps/ROOT/skins/flamingo/drawer.vm
(I’m running the Docker image xwiki:lts-mysql-tomcat)
The above is with the line
oidc.endpoint.logout=https://KEYCLOAKSERVER/auth/realms/demo/protocol/openid-connect/logout
commented out in xwiki.properties. I tried with this line active but I did not see a change in behavior.
1 Like
@MartinBuber
Just for the record: Does ist work? If yes, one should update the official documentation.