Hi,Everybody is good
I upgraded from 10.4 to 11.2.
Download the OpenID Connect Authenticator extension package and make changes. I found that the login will still jump to the XWiki login page. Why is this?
thank you
Hi,Everybody is good
I upgraded from 10.4 to 11.2.
Download the OpenID Connect Authenticator extension package and make changes. I found that the login will still jump to the XWiki login page. Why is this?
thank you

What do you exactly mean by that ? You installed it with Extension Manager or you just downloaded the jar and copied it in WEB-INF/lib ?
I installed it with Extension Manager and modify the xwiki.properties parameter.
But the last redirect page is 401
Could you indicate the exact steps to reproduce this issue ?
You just access the home page and end up directly on failing login page ? When you don’t configure anything you are supposed to get a form asking you the OIDC provider to use.
I have a similar problem. I have the configuration set up on one site where it works without issues but on a new site I can’t get past the 401.
oidc.endpoint.authorization=https://my-keycloak-url/auth/realms/km/protocol/openid-connect/auth
oidc.endpoint.token=https://my-keycloak-url/auth/realms/km/protocol/openid-connect/token
oidc.endpoint.token.auth_method=client_secret_basic
oidc.endpoint.userinfo=https://my-keycloak-url/auth/realms/km/protocol/openid-connect/userinfo
oidc.endpoint.userinfo.method=get
#-# The pattern to use to generate the XWiki user name
oidc.user.nameFormater=${oidc.user.subject.clean}
#-# The OpenID Connect client identifier used by the authenticator (sub is a persistent id)
oidc.idtokenclaims=sub
#-# The custom claims to request to the provider for the UserInfo
oidc.userinfoclaims=xwiki_groups,sub,iss,auth_time,name,given_name,family_name,preferred_username,email
oidc.groups.claim=xwiki_groups
oidc.groups.allowed=XWikiAllGroup
#-# The client identifier used by the authentication.
oidc.clientid=wiki.MY.SITE
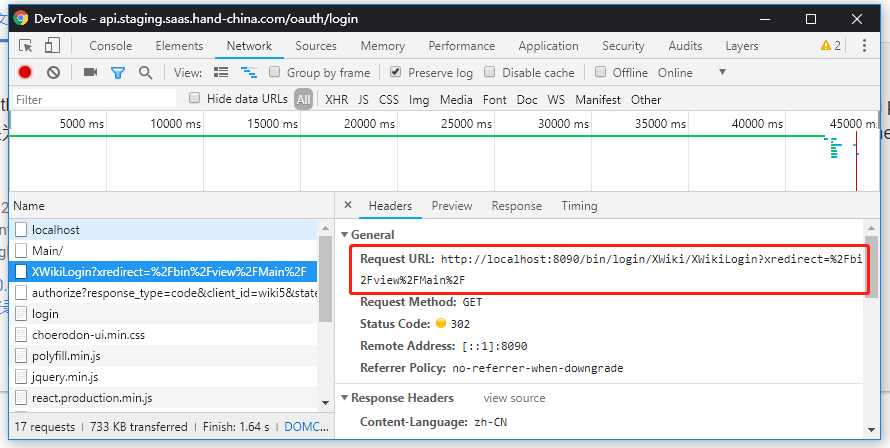
The client ‘stops’ at https://wiki.MY.SITE/bin/login/XWiki/XWikiLogin?xredirect=%2Fbin%2Fview%2FMain%2F with a 401
I don’t see any errors in the logs.
Note that I had to set oidc.endpoint.userinfo.method=get otherwise the server would throw an “HTTP method must not be null” error.
How can I find out why it returns the 401? The response parameters even contain Location: https://wiki.MY.SITE/bin/view/Main/ for the redirect. When I go to https://wiki.MY.SITE/bin/view/Main/ I can see that the user was logged in correctly.
Thanks, this is now fixed in 1.14.2.
I would suggest to enable debug log to get more details on what exactly happen in that authenticator. Just added https://extensions.xwiki.org/xwiki/bin/view/Extension/OpenID%20Connect/OpenID%20Connect%20Authenticator/#HEnableDEBUGlog.
It’s very weird then since https://wiki.MY.SITE/bin/login/XWiki/XWikiLogin is supposed to redirect automatically to the wiki home page when the user is already authenticated (at least it does for me).
Thanks for the quick reply! I’ve updated to 1.14.2 and enabled tracing. Here is the log:
2019-04-10 12:20:02,253 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG i.OIDCResourceReferenceHandler - OIDC: Reference: [path = authenticator/callback, endpoint = authenticator, pathSegments = [callback]]
2019-04-10 12:20:02,253 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG c.o.a.i.e.CallbackOIDCEndpoint - OIDC callback: starting with request [http://172.21.0.3:8080/oidc/authenticator/callback]
2019-04-10 12:20:02,254 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG c.o.a.i.e.CallbackOIDCEndpoint - OIDC Token request (https://key.MY.SITE/auth/realms/km/protocol/openid-connect/token?code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16&redirect_uri=https%3A%2F%2Fwiki.MY.SITE%3A443%2Foidc%2Fauthenticator%2Fcallback&grant_type=authorization_code&client_id=wiki.MY.SITE,null)
2019-04-10 12:20:02,285 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG c.o.a.i.e.CallbackOIDCEndpoint - OIDC Token response ({"access_token":"<DATA>.<DATA>.<DATA>","expires_in":300,"refresh_expires_in":1800,"refresh_token":"<DATA>.<DATA>.<DATA>","token_type":"bearer","id_token":"<DATA>.<DATA>.<DATA>","not-before-policy":0,"session_state":"18ff4702-aa2f-4432-aca2-b43d8feae620","scope":"openid email profile phone address"}
)
2019-04-10 12:20:02,287 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - OIDC user info request (https://key.MY.SITE/auth/realms/km/protocol/openid-connect/userinfo,<DATA>.<DATA>.<DATA>)
2019-04-10 12:20:02,290 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - OIDC user info request (https://key.MY.SITE/auth/realms/km/protocol/openid-connect/userinfo?null)
2019-04-10 12:20:02,334 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - OIDF user info response ({"sub":"7dc15d82-a350-4018-a883-774168b10250","email_verified":true,"address":{},"name":"foo","groups":["employee"],"preferred_username":"foo","given_name":"foo","xwiki_groups":["XWikiAllGroup","employee","XWikiAdminGroup"],"family_name":"bar","email":"foo@MY.SITE"}
)
2019-04-10 12:20:02,351 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - Updating XWiki claims
2019-04-10 12:20:02,352 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - Getting groups sent by the provider associated with claim [xwiki_groups]
2019-04-10 12:20:02,352 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - The provider sent the following groups: ["XWikiAllGroup","employee","XWikiAdminGroup"]
2019-04-10 12:20:02,353 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - Updating group membership for the user [XWiki.7dc15d82-a350-4018-a883-774168b10250]
2019-04-10 12:20:02,356 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG o.x.c.o.a.i.OIDCUserManager - The user belongs to following XWiki groups: [XWiki.XWikiAdminGroup, XWiki.XWikiAllGroup, XWiki.employee]
2019-04-10 12:20:02,356 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG c.o.a.i.e.CallbackOIDCEndpoint - OIDC callback: principal=[SimplePrincipal[name = 'xwiki:XWiki.7dc15d82-a350-4018-a883-774168b10250']]
2019-04-10 12:20:02,357 [https://wiki.MY.SITE/oidc/authenticator/callback?state=njdqEeipOMlFO__eHwFkYIBJaTUJQh4ZsUum2H23EFU&session_state=18ff4702-aa2f-4432-aca2-b43d8feae620&code=6a4a4315-a09b-4731-98e6-994afd9cc332.18ff4702-aa2f-4432-aca2-b43d8feae620.10279957-446e-4342-bf3b-6afc6d106c16] DEBUG c.o.a.i.e.CallbackOIDCEndpoint - OIDC callback: redirect=[https://wiki.MY.SITE/bin/login/XWiki/XWikiLogin?xredirect=%2Fbin%2Fview%2FMain%2F]
The “OIDC callback: redirect” entry contains the URL I see in the browser, but for some reason the status code is 401 instead of 301.
Here are the response headers (xwiki is behind a reverse proxy that adds https):
HTTP/1.1 401
Server: nginx
Date: Wed, 10 Apr 2019 12:20:02 GMT
Content-Type: text/html;charset=UTF-8
Content-Length: 0
Connection: keep-alive
Content-Script-Type: text/javascript
Pragma: no-cache
Cache-Control: no-cache
Expires: Wed, 31 Dec 1969 23:59:59 GMT
Location: https://wiki.keeman.world/bin/view/Main/
Content-Language: enThis is a very weird response. Looks like a redirect but with a 401 http code, could it be caused by nginx rewrite ? I would really suggest to try directly on 8080 port to see if you have the same issue.
Yes it’s weird but the 401 is not coming from the reverse proxy. The logs from tomcat show 401 as well:
172.16.0.4 - - [10/Apr/2019:14:26:52 +0000] "GET /bin/login/XWiki/XWikiLogin?xredirect=%2Fbin%2Fview%2FMain%2F HTTP/1.0" 302 -
172.16.0.4 - - [10/Apr/2019:14:26:53 +0000] "GET /oidc/authenticator/callback?state=UiecLzooxkhkwLVGOtBHGMTLQMMsqg-hXjo_ZfnEFTw&session_state=c5520aaf-4d97-4b00-8a18-579a2a691910&code=71407ce3-691f-4428-8349-4ad37c2e392f.c5520aaf-4d97-4b00-8a18-579a2a691910.10279957-446e-4342-bf3b-6afc6d106c16 HTTP/1.0" 302 -
172.16.0.4 - - [10/Apr/2019:14:26:53 +0000] "GET /bin/login/XWiki/XWikiLogin?xredirect=%2Fbin%2Fview%2FMain%2F HTTP/1.0" 401 -
And @Peter also mentioned the 401.
I’m running the xwiki:11.2-postgres-tomcat docker distribution.
hi,
I’m also running the xwiki: 11.2-tomcat docker.
I downloaded the oidc code from github and did the debugging.
I found that the user was successfully authorized, but the last redirect address was wrong,so I modified the code of the project oidc-authenticator and changed the last redirect address.
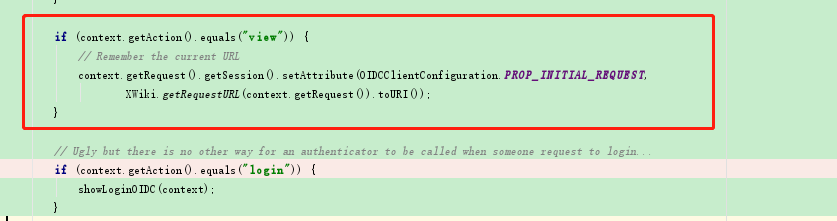
step 1
Modification method org.xwiki.contrib.oidc.auth.OIDCAuthServiceImpl.checkAuthOIDC()
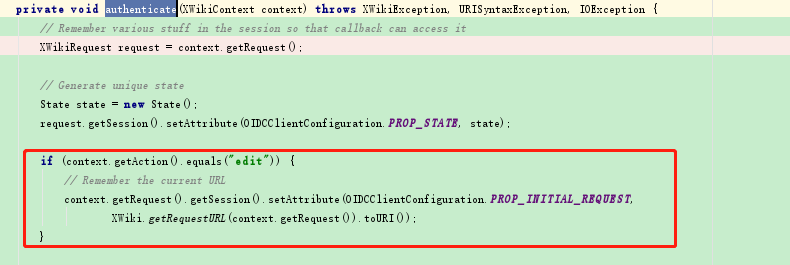
step 2
Modification method
org.xwiki.contrib.oidc.auth.OIDCAuthServiceImpl.authenticate()
Compile the project oidc-authenticator into a jar package to replace the old one, restart the docker, it can be solved.
What is the specific cause, I still don’t know, this is just a temporary solution.
I hope to help you.