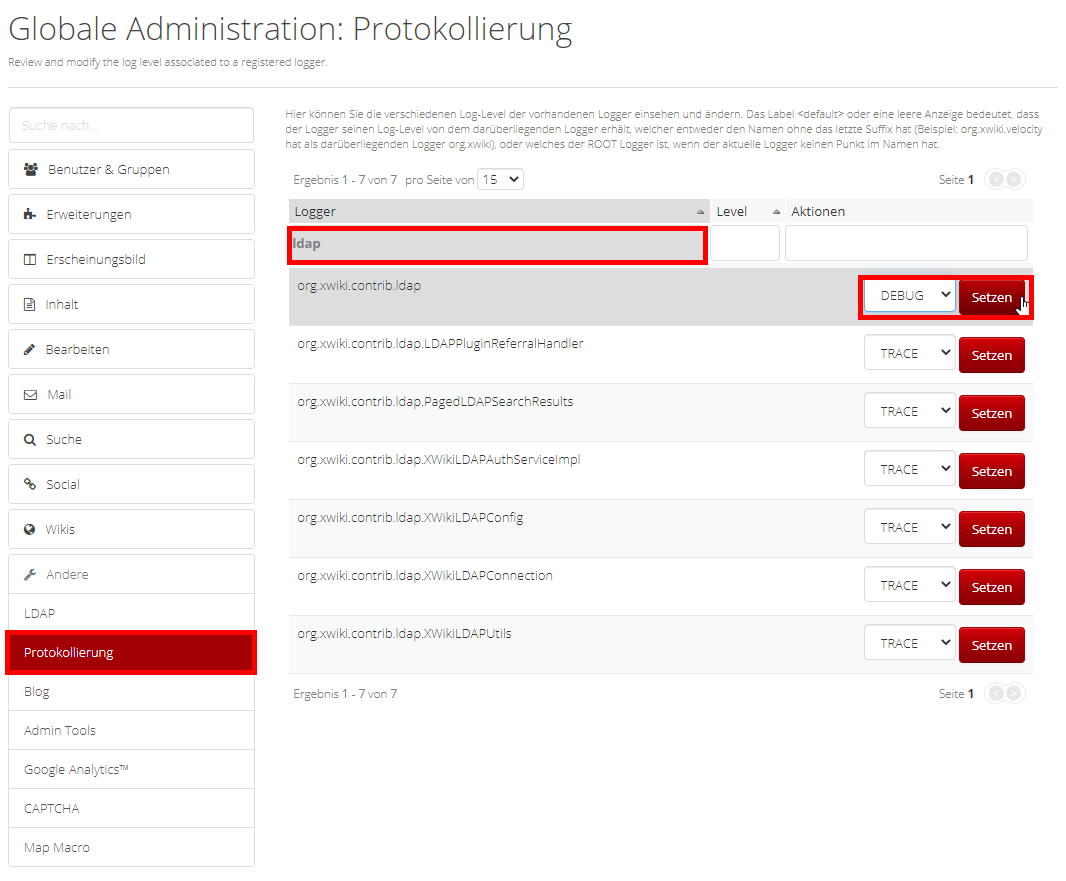
Hi jwielsch,
sure. Here they are:
2020-10-30 15:00:52,047 [XWiki initialization] INFO .HibernateDataMigrationManager - Storage schema updates and data migrations are enabled
2020-10-30 15:00:52,213 [XWiki initialization] INFO .HibernateDataMigrationManager - No data migration to apply for wiki [xwiki] currently in version [1138000]
2020-10-30 15:00:52,214 [XWiki initialization] INFO .HibernateDataMigrationManager - Checking Hibernate mapping and updating schema if needed for wiki [xwiki]
2020-10-30 15:01:03,290 [org.xwiki.search.solr.internal.job.IndexerJob@76164bc0([solr, indexer])] INFO o.x.s.s.i.j.IndexerJob - Starting job of type [solr.indexer] with identifier [[solr, indexer]]
2020-10-30 15:01:05,724 [org.xwiki.search.solr.internal.job.IndexerJob@76164bc0([solr, indexer])] INFO o.x.s.s.i.j.IndexerJob - 1721 documents added, 1721 deleted and 0 updated during the synchronization of the Solr index.
2020-10-30 15:01:05,725 [org.xwiki.search.solr.internal.job.IndexerJob@76164bc0([solr, indexer])] INFO o.x.s.s.i.j.IndexerJob - Finished job of type [solr.indexer] with identifier [[solr, indexer]]
2020-10-30 15:01:05,880 [http://companywiki:8082/xwiki/bin/view/Main/] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:05,899 [http://companywiki:8082/xwiki/bin/view/Main/] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:06,009 [http://companywiki:8082/xwiki/bin/login/XWiki/XWikiLogin?srid=JdNiA9gR&xredirect=%2Fxwiki%2Fbin%2Fview%2FMain%2F%3Fsrid%3DJdNiA9gR] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:06,010 [http://companywiki:8082/xwiki/bin/login/XWiki/XWikiLogin?srid=JdNiA9gR&xredirect=%2Fxwiki%2Fbin%2Fview%2FMain%2F%3Fsrid%3DJdNiA9gR] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:14,054 [http://companywiki:8082/xwiki/bin/skin/skins/flamingo/flamingo.min.js?cache-version=1597737344000&language=de] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:14,054 [http://companywiki:8082/xwiki/bin/skin/skins/flamingo/flamingo.min.js?cache-version=1597737344000&language=de] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:14,061 [http://companywiki:8082/xwiki/bin/skin/resources/js/xwiki/xwiki-min.js?cache-version=1597737354000&defer=false&language=de] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:14,061 [http://companywiki:8082/xwiki/bin/skin/resources/js/xwiki/xwiki-min.js?cache-version=1597737354000&defer=false&language=de] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:14,088 [http://companywiki:8082/xwiki/bin/skin/resources/uicomponents/async/async.js?cache-version=1597737354000] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:14,088 [http://companywiki:8082/xwiki/bin/skin/resources/uicomponents/async/async.js?cache-version=1597737354000] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:14,099 [http://companywiki:8082/xwiki/bin/skin/resources/js/scriptaculous/effects.js?cache-version=1597737352000] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:14,099 [http://companywiki:8082/xwiki/bin/skin/resources/js/scriptaculous/effects.js?cache-version=1597737352000] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:14,279 [http://companywiki:8082/xwiki/bin/skin/resources/icons/xwiki/noavatar.png?cache-version=1597736868000] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:14,279 [http://companywiki:8082/xwiki/bin/skin/resources/icons/xwiki/noavatar.png?cache-version=1597736868000] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:22,220 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:22,221 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - remoteUserParser: null
2020-10-30 15:01:22,247 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - ldap_group_classes: [groupofnames, posixgroup, apple-group, groupofuniquenames, dynamicgroup, groupwisedistributionlist, group, dynamicgroupaux]
2020-10-30 15:01:22,247 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - ldap_group_memberfields: [uniquemember, memberuid, member]
2020-10-30 15:01:22,248 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - LDAP authentication failed: LDAP not activ
2020-10-30 15:01:22,248 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - Trying authentication against XWiki DB
2020-10-30 15:01:22,311 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - LDAP authentication failed for user [xwikiadtestuser]
2020-10-30 15:01:22,311 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] WARN nticationFailureLoggerListener - Authentication failure with login [xwikiadtestuser]
2020-10-30 15:01:22,346 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:29,846 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:29,846 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - remoteUserParser: null
2020-10-30 15:01:29,846 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - ldap_group_classes: [groupofnames, posixgroup, apple-group, groupofuniquenames, dynamicgroup, groupwisedistributionlist, group, dynamicgroupaux]
2020-10-30 15:01:29,846 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - ldap_group_memberfields: [uniquemember, memberuid, member]
2020-10-30 15:01:29,846 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - LDAP authentication failed: LDAP not activ
2020-10-30 15:01:29,846 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - Trying authentication against XWiki DB
2020-10-30 15:01:29,847 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - LDAP authentication failed for user [xwikiadtestuser]
2020-10-30 15:01:29,847 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] WARN nticationFailureLoggerListener - Authentication failure with login [xwikiadtestuser]
2020-10-30 15:01:29,847 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:37,067 [XWiki Solr index thread] WARN o.a.p.p.f.PDType1Font - Using fallback font LiberationSans for base font Symbol
2020-10-30 15:01:37,067 [XWiki Solr index thread] WARN o.a.p.p.f.PDType1Font - Using fallback font LiberationSans for base font ZapfDingbats
2020-10-30 15:01:37,569 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c74 (74) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:37,571 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c76 (76) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:37,572 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c77 (77) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:37,640 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c71 (71) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:38,434 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c74 (74) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:38,436 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c76 (76) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:38,436 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c77 (77) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:38,481 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for c71 (71) in font VUNAPB+Wingdings-Regular
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - The provided user is null. We don’t try to authenticate, it probably means the user is in non logged mode.
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - remoteUserParser: null
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - ldap_group_classes: [groupofnames, posixgroup, apple-group, groupofuniquenames, dynamicgroup, groupwisedistributionlist, group, dynamicgroupaux]
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG o.x.c.l.XWikiLDAPConfig - ldap_group_memberfields: [uniquemember, memberuid, member]
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - LDAP authentication failed: LDAP not activ
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - Trying authentication against XWiki DB
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - LDAP authentication failed for user [xwikiadtestuser]
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] WARN nticationFailureLoggerListener - Authentication failure with login [xwikiadtestuser]
2020-10-30 15:01:58,215 [http://companywiki:8082/xwiki/bin/loginsubmit/XWiki/XWikiLogin] DEBUG x.c.l.XWikiLDAPAuthServiceImpl - XWikiUser: null
2020-10-30 15:01:59,430 [XWiki Solr index thread] WARN o.a.p.p.f.PDTrueTypeFont - Using fallback font ‘LiberationSerif-Bold’ for ‘TimesNewRomanPS-BoldMT’
2020-10-30 15:01:59,431 [XWiki Solr index thread] WARN o.a.p.p.f.PDTrueTypeFont - Using fallback font ‘LiberationSerif’ for ‘TimesNewRomanPSMT’
2020-10-30 15:01:59,459 [XWiki Solr index thread] WARN o.a.p.p.f.PDTrueTypeFont - Using fallback font ‘LiberationSerif-BoldItalic’ for ‘TimesNewRomanPS-BoldItalicMT’
2020-10-30 15:01:59,551 [XWiki Solr index thread] WARN o.a.p.p.f.PDTrueTypeFont - Using fallback font ‘LiberationSerif-Bold’ for ‘TimesNewRomanPS-BoldMT’
2020-10-30 15:01:59,552 [XWiki Solr index thread] WARN o.a.p.p.f.PDTrueTypeFont - Using fallback font ‘LiberationSerif’ for ‘TimesNewRomanPSMT’
2020-10-30 15:01:59,588 [XWiki Solr index thread] WARN o.a.p.p.f.PDTrueTypeFont - Using fallback font ‘LiberationSerif-BoldItalic’ for ‘TimesNewRomanPS-BoldItalicMT’
2020-10-30 15:02:00,423 [XWiki Solr index thread] WARN o.a.f.t.CmapSubtable - Format 14 cmap table is not supported and will be ignored
2020-10-30 15:02:00,867 [XWiki Solr index thread] WARN o.a.f.t.CmapSubtable - Format 14 cmap table is not supported and will be ignored
2020-10-30 15:02:01,760 [XWiki Solr index thread] WARN o.a.p.p.f.PDSimpleFont - No Unicode mapping for barb1left (1) in font HLVIJR+Wingdings3