Hello,
tests ongoing in XWiki 15.10, I have been regularly seeing warnings about security vulnerabilities along the tests in the previous versions up to now. I always check for extension updates but it is seldom extension updates that make these warnings go away.
So now I would like to have information wether or not it should be solved upstream by the XWiki team, thus providing some updates through the normal stream?
Or if another method is advised?
Here is a screenshot for what I get today.
Thank you for your information!
btw, https://dev.xwiki.org/xwiki/bin/view/Community/Discuss#HMailingLists =>
=> https://lists.xwiki.org/mailman/listinfo/security the page does not exist.
1 Like
Indeed, the documentation was a bit outdated, just fixed it.
1 Like
I have tried to fix the security vulnerabilities by myself, with the help of my colleagues. Up to now it is not satisfactory, as it can’t be done in a way which would follow a clear process.
Once, we hit a link following a lead with the hyperlinks and updated manually, another time recently I removed these two items:
- adal4j 1.6.7
- JSON Small and Fast Parser
which I was not sure was a good idea (still unsure). It has solved the security warning but warnings were there again not many days after.
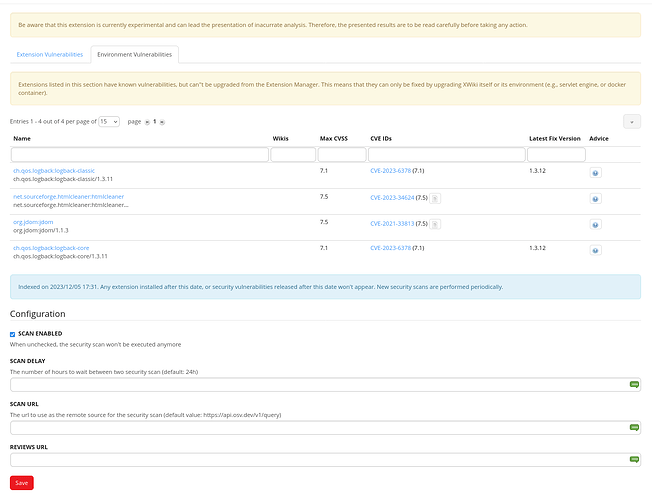
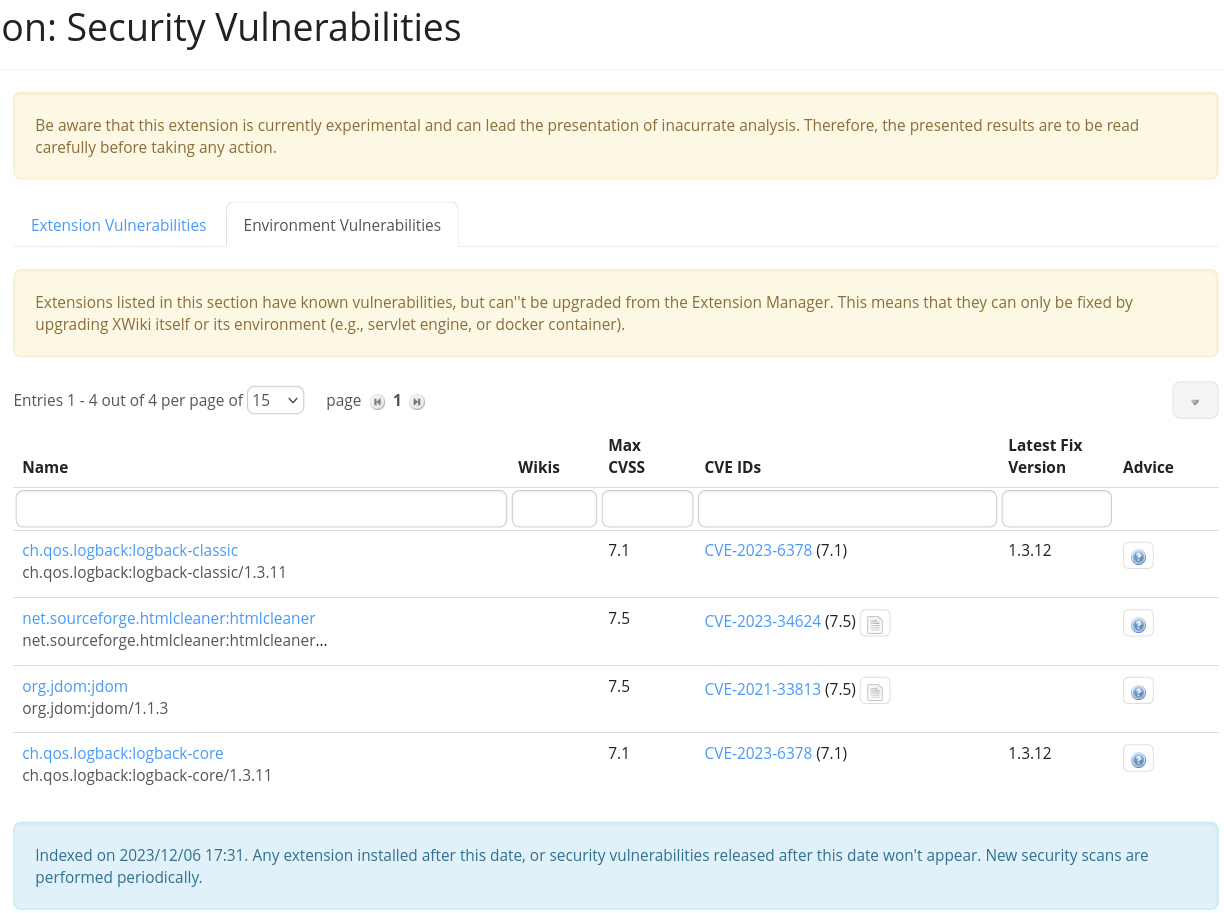
Here after in text mode are the ones listed in the screenshot:
ch.qos.logback:logback-classic
ch.qos.logback:logback-classic/1.3.11 7.1 CVE-2023-6378 (7.1)1.3.12
net.sourceforge.htmlcleaner:htmlcleaner
net.sourceforge.htmlcleaner:htmlcleaner/2.24 7.5 CVE-2023-34624 (7.5)
org.jdom:jdom
org.jdom:jdom/1.1.3 7.5 CVE-2021-33813 (7.5)
ch.qos.logback:logback-core
ch.qos.logback:logback-core/1.3.11 7.1 CVE-2023-6378 (7.1) 1.3.12
So is it usual? Is it endless? 
Is it concerning?
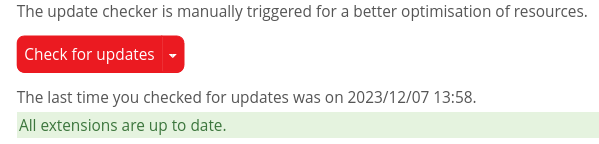
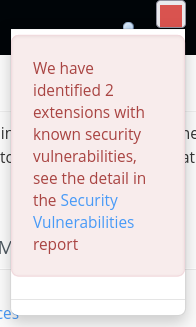
I have checked again today if some extensions were to be updated, but they are all up to date, and the message about 2 extensions having security issues is still there.
There is also still the warning saying:
Be aware that this extension is currently experimental and can lead the presentation of inacurrate analysis. Therefore, the presented results are to be read carefully before taking any action.
Here are a few pics taken minutes ago, extensions update status, warning message, page where the supposed vulnerabilities should be found:
is it ok to ignore? Should it be addressed and if so, how?
According to logback news, CVE-2023-6378 only affects setups where a logback receiver component is accessible by an attacker. This is not a setup we use in XWiki. Nevertheless, the 15.10.1 release that is planned for Monday, December 11th will include an updated logback version that doesn’t have this vulnerability. The other dependencies are harder to update/remove (there is no update for this jdom version available) but according to our analysis that is linked when you click on the icon next to the CVE the vulnerabilities shouldn’t have a big impact in XWiki.
Note that XWiki 15.10 doesn’t bundle the security vulnerabilities application that you’re showing here anymore.
1 Like
Thanks a lot @MichaelHamann for the info and news. I’ll look into remove this vulnerabilites application then. Is it possible to do that without performing a fresh install?
You can just uninstall it in the extension manager. Search for “Security Vulnerabilities API” and uninstall it. This should catch everything related to it. This should also have been proposed in the distribution wizard when you upgraded to XWiki 15.9.
1 Like
@MichaelHamann thank you very much, I have followed your advice, no more warnings!
1 Like